Challenges Kubernetes admins faces
Suppose a developer that made changes to Kubernetes configurations files, to deploy their objects, and they push their configuration file on git repo. And it caused a failure in production. Wouldn't it be cool to figure out these misconfigurations before the production? Here comes Datree to the rescue.
What is Datree
Datree is an open-source CLI tool for engineers to use in creating more stable and secure Kubernetes configurations. By revealing misconfigurations in the early stages of the pipeline.
Downloading and configuring Datree CLI
Before downloading the Datree Cli, You have to sign up to get the curl command to download Datree in your local.
To download and Install Datree, just follow these steps:
1)Open your terminal.
2)And type this command :
For Linux/macOS:
> curl https://get.datree.io | /bin/bash
For Window:
iwr -useb https://get.datree.io/windows_install.ps1 | iex
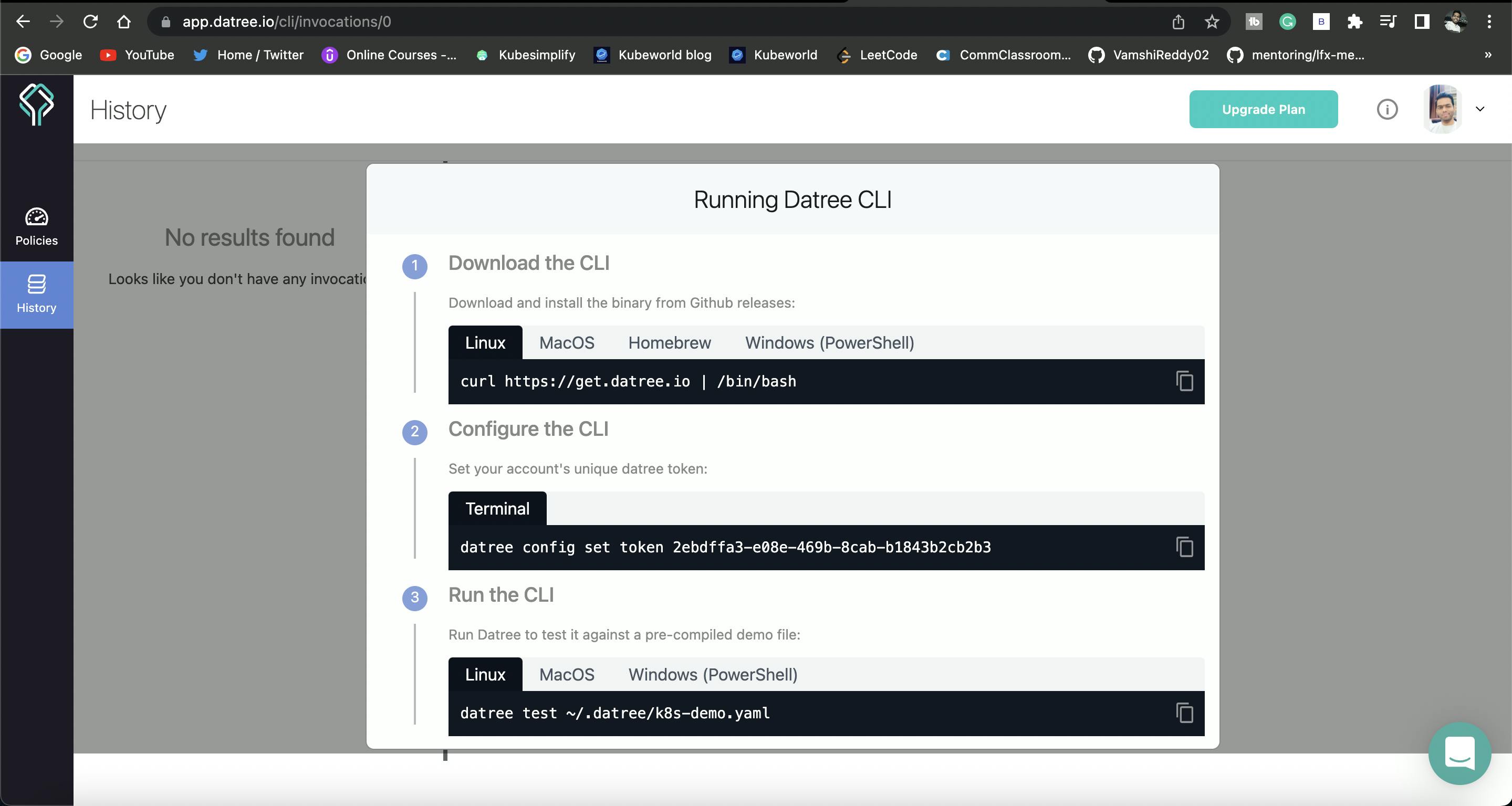 3)The next step is to Configure the CLI, So basically any changes that you are going to make via this Graphical user interface, in real-time will be visible in your repository. That is why we are connecting with this token that Datree has provided. So everyone gets their token.
3)The next step is to Configure the CLI, So basically any changes that you are going to make via this Graphical user interface, in real-time will be visible in your repository. That is why we are connecting with this token that Datree has provided. So everyone gets their token.
Running the YAML File
Now to test it, we need a Kubernetes configuration file. By default, Datree offers a demo Kubernetes configuration file for you to test out the tool.
apiVersion: apps/v1
kind: Deployment
metadata:
name: rss-site
namespace: test
labels:
owner: --
environment: prod
app: web
spec:
replicas: 3
selector:
matchLabels:
app: web
template:
metadata:
namespace: test
labels:
app: we
spec:
containers:
- name: front-end
image: nginx:latest
readinessProbe:
tcpSocket:
port: 8080
initialDelaySeconds: 5
periodSeconds: 10
resources:
requests:
memory: "64Mi"
cpu: "64m"
limits:
cpu: "500m"
ports:
- containerPort: 80
- name: rss-reader
image: datree/nginx@sha256:45b23dee08af5e43a7fea6c4cf9c25ccf269ee113168c19722f87876677c5cb2
livenessProbe:
httpGet:
path: /healthz
port: 8080
httpHeaders:
- name: Custom-Header
value: Awesome
readinessProbe:
tcpSocket:
port: 8080
initialDelaySeconds: 5
periodSeconds: 10
resources:
requests:
cpu: "64m"
memory: "128Mi"
limits:
memory: "128Mi"
ports:
- containerPort: 88
Type this command to test this demo Kubernetes file:
$ datree test ~/.datree/k8s-demo.yaml
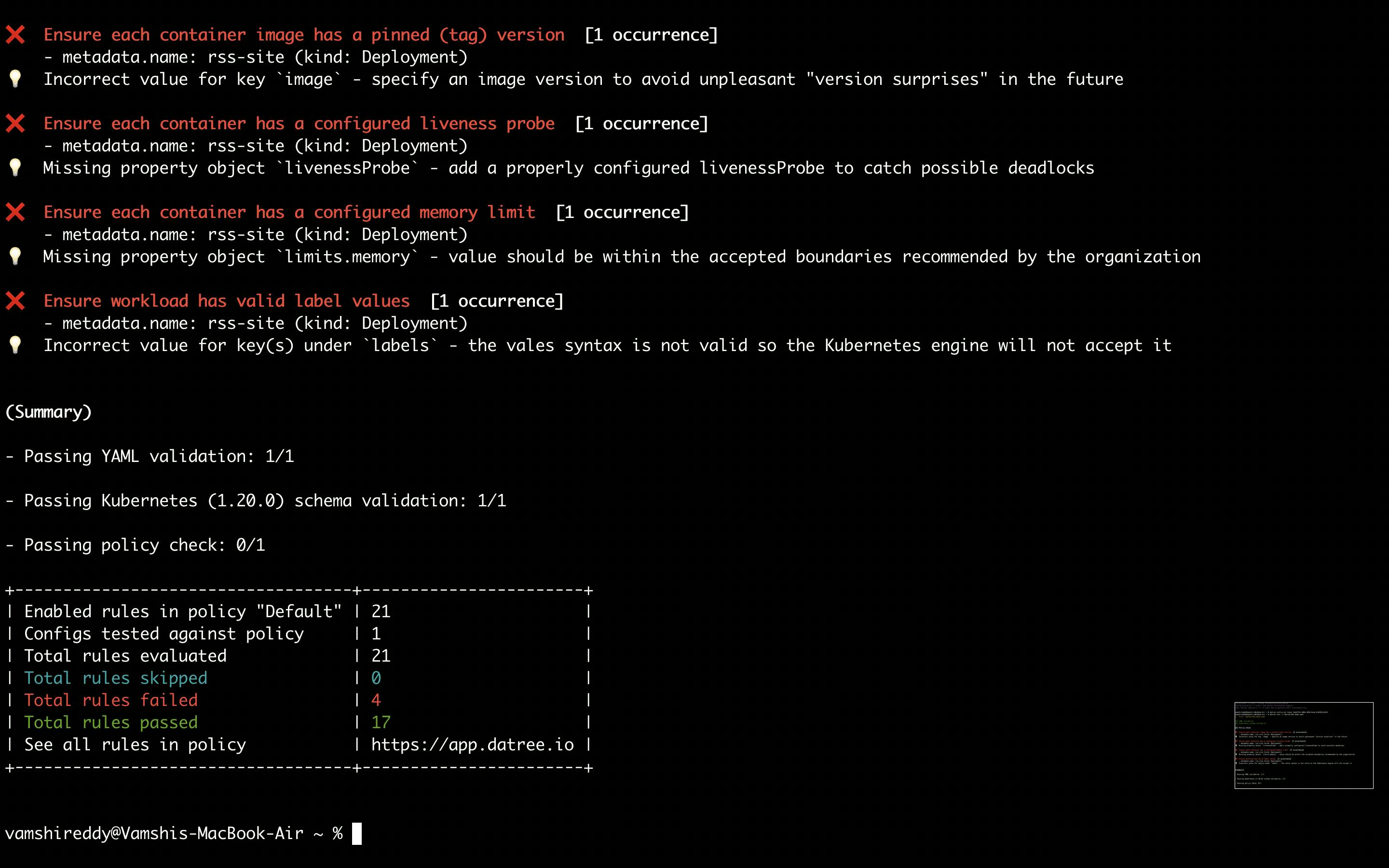
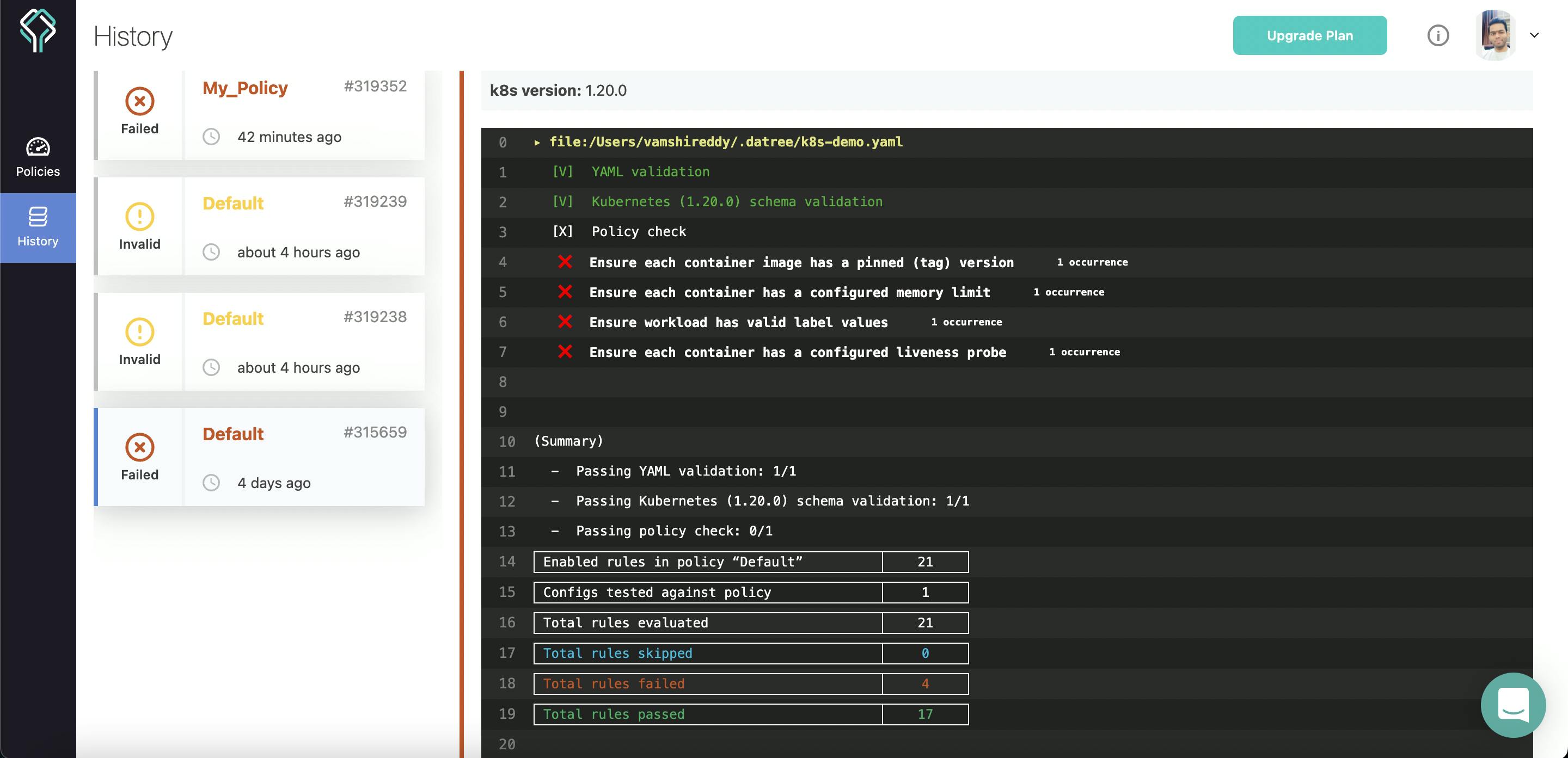
As you can see above out of 21 policy checks, 4 rules are failing.
You can find the history of your test in your Datree dashboard. How cool it is!
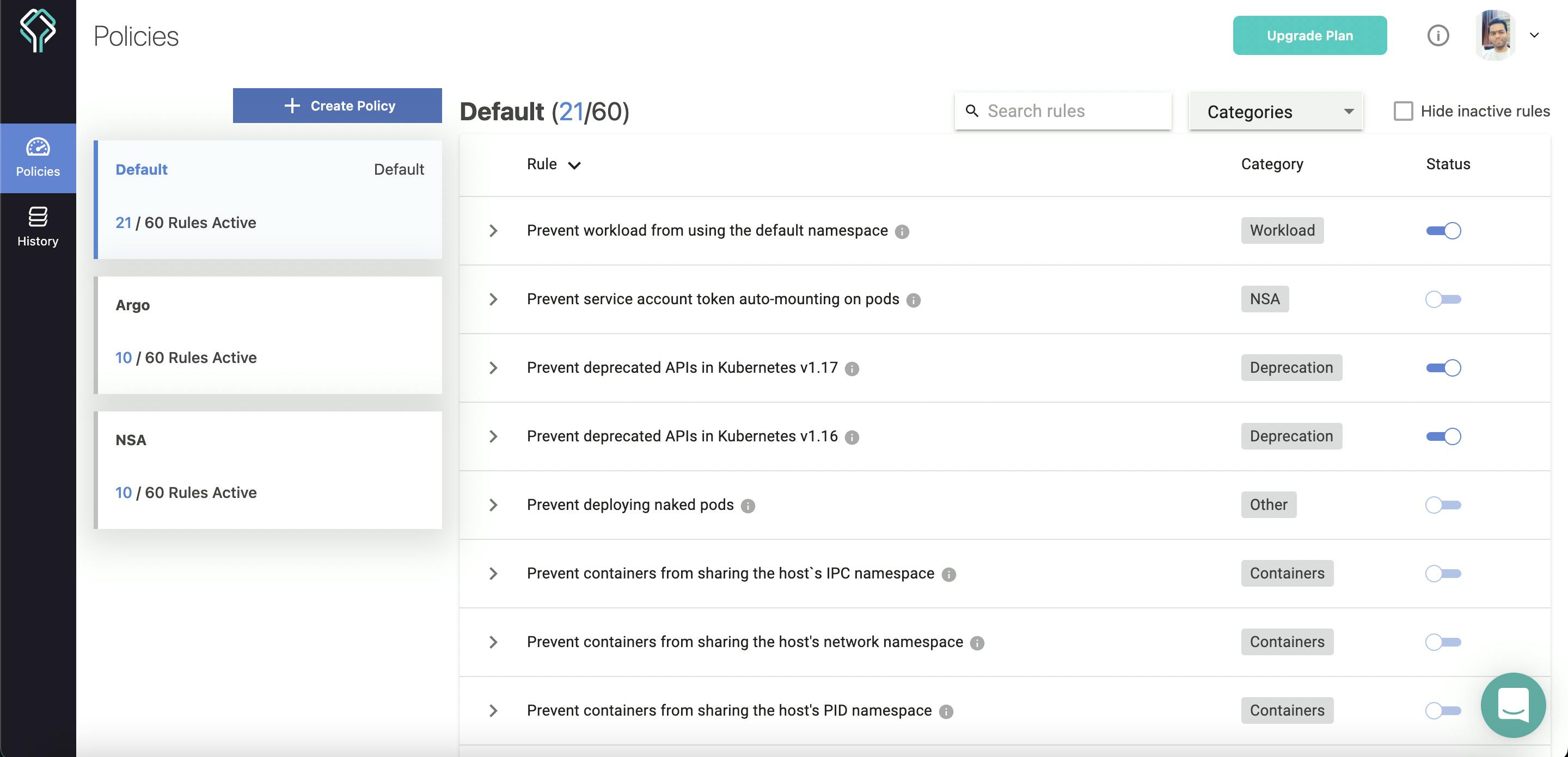
Now by default Datree provides more than 60 rules for testing and these rules are categorised into Argo, Container, CronJob, Custom, Deprecation, Network, NSA, Security, Workload and Other.
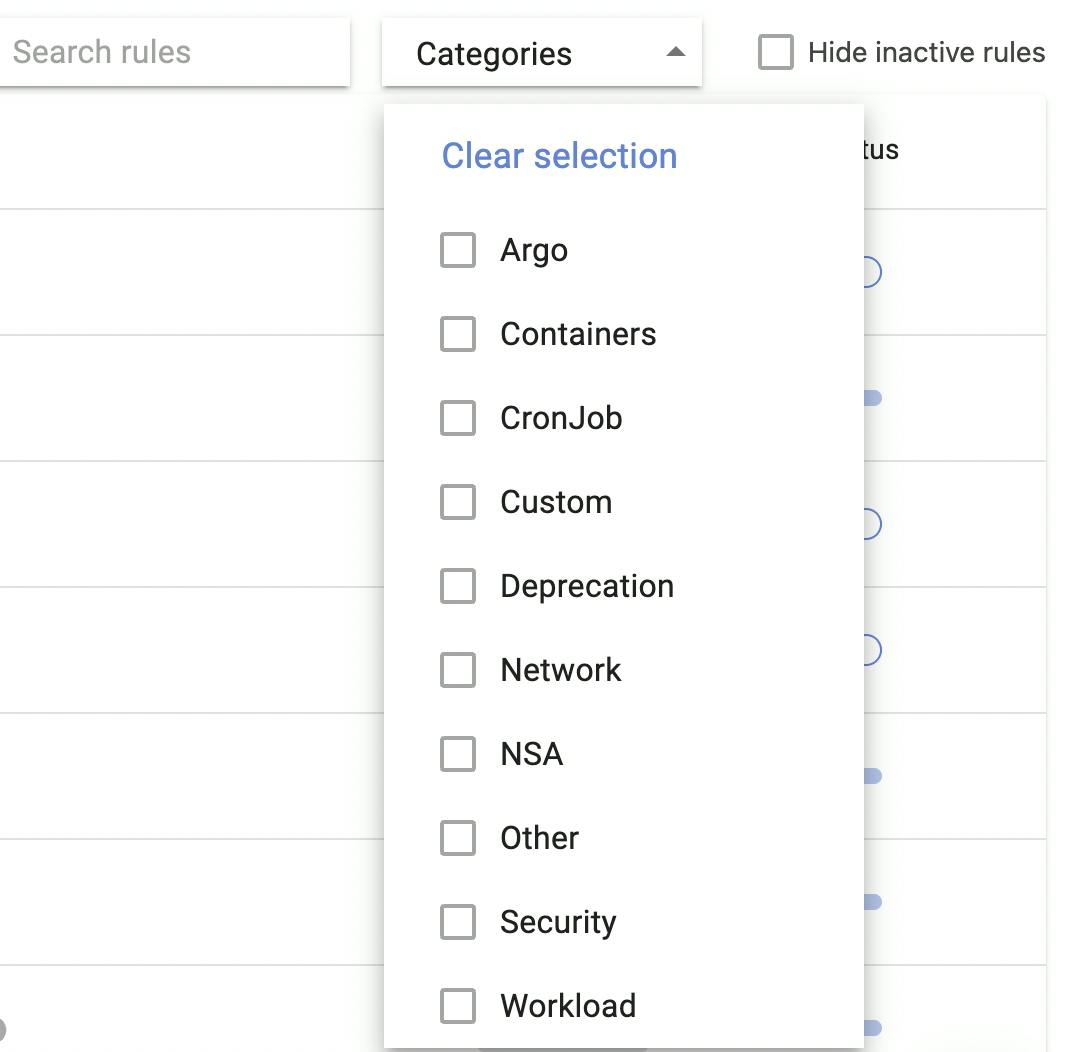
If you want, you can check and uncheck some of the rules according to your convenience and also you can change the error message of various rules.
Schema validation
Before running the policy checks, Datree performs schema validation checks for a file to check whether the file does not any typos or errors in the structure of your YAML file.
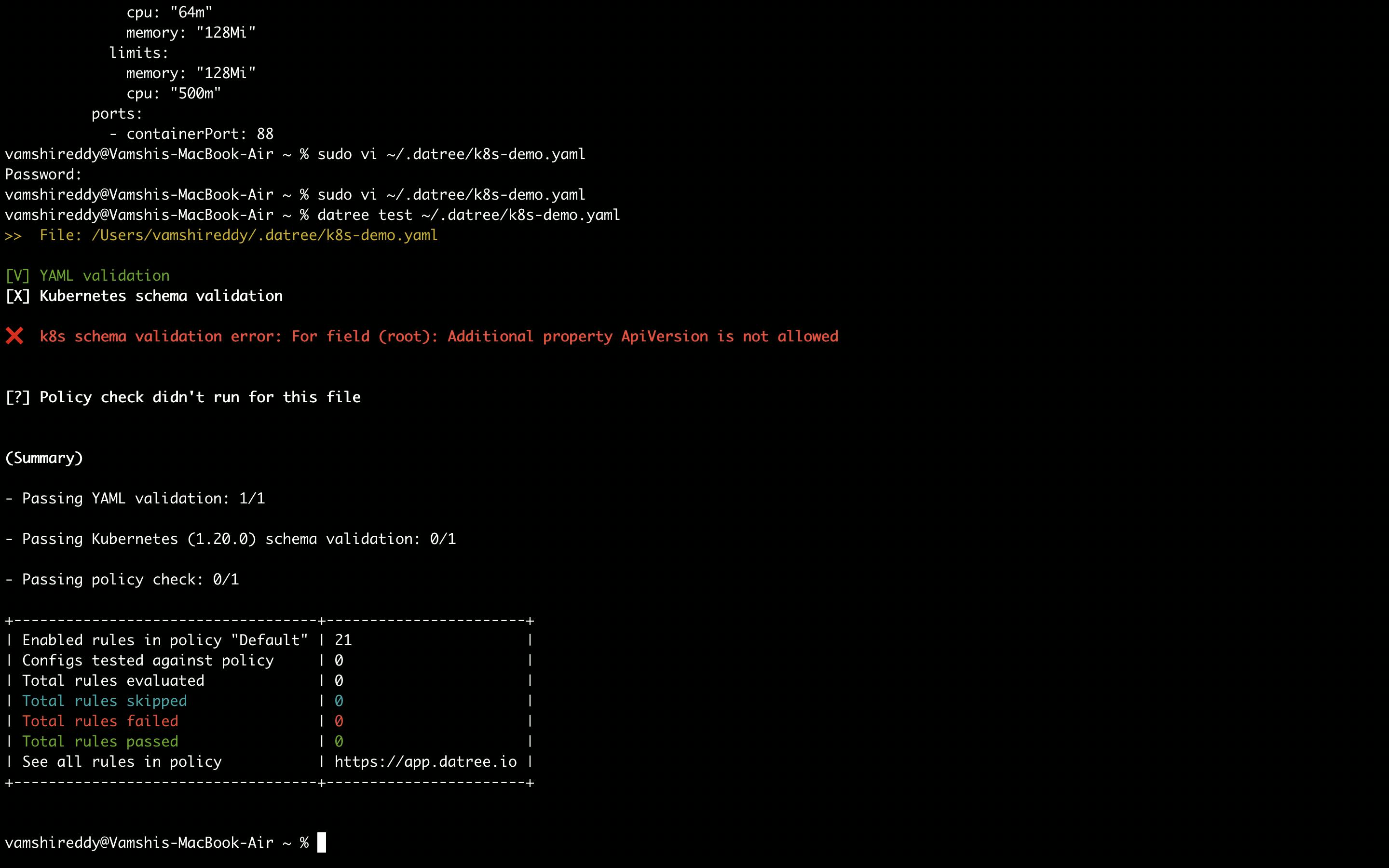 When there are any typos in the YAML file.
When there are any typos in the YAML file.
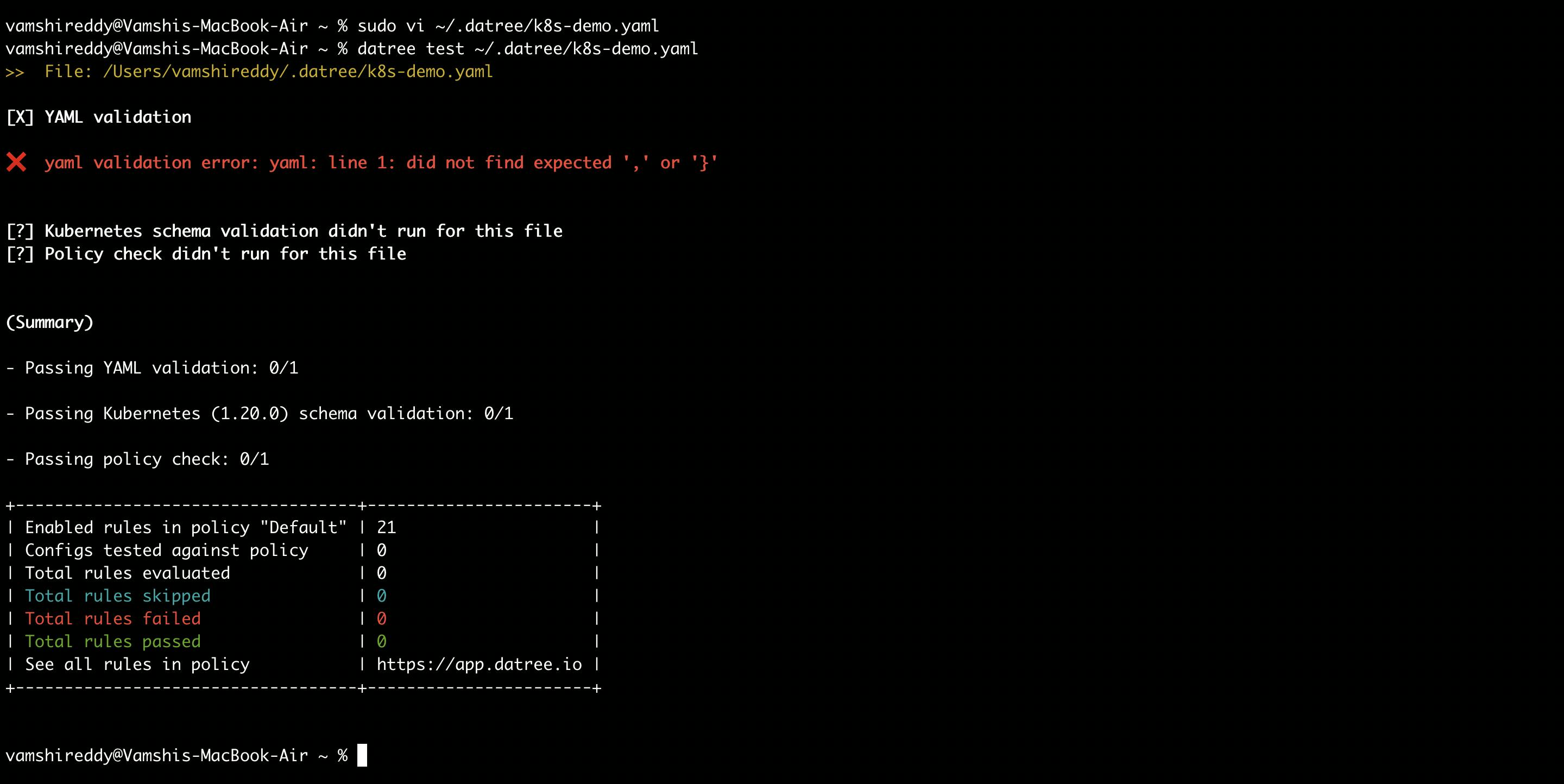 When there is an error in the structure of your YAML file
When there is an error in the structure of your YAML file
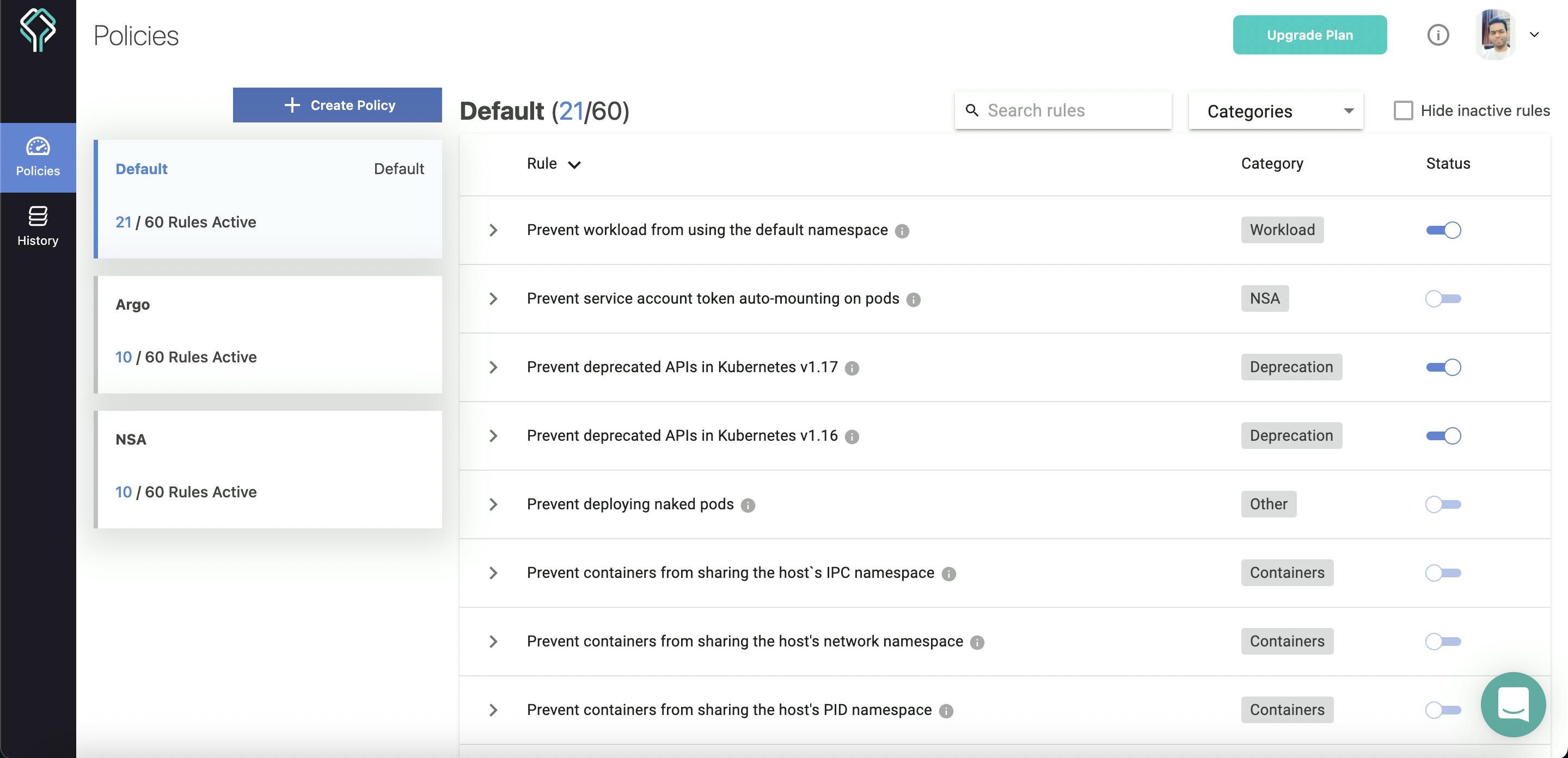
4) Creating your Policies
Datree has these amazing features which I find most interesting i.e, creating our own policies. You can add different rules configured, giving each policy its own use cases.
Steps to create your own policy:
1) Go to Datree dashboard and click on +CREATE POLICY.
2) Here you can give its name.
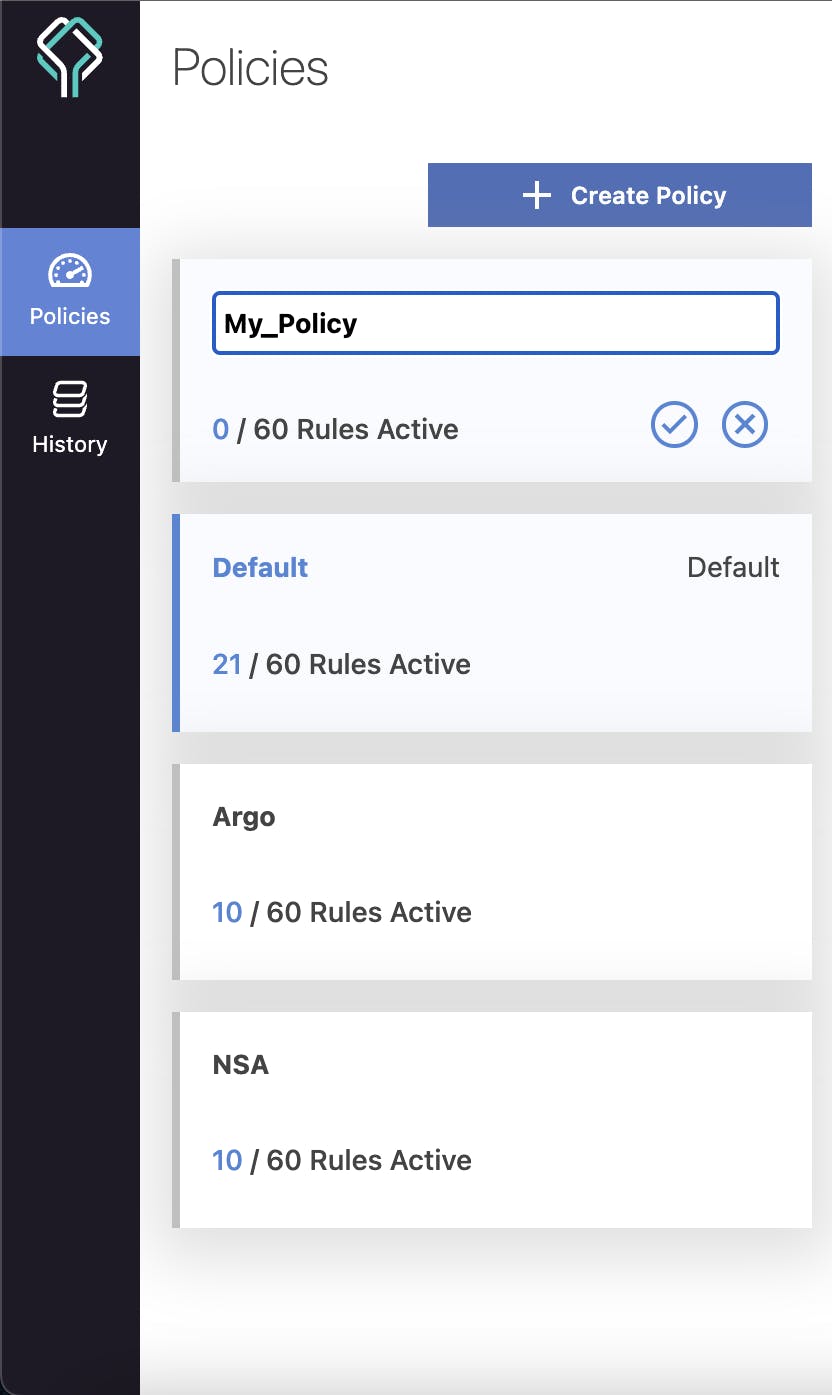
3) Once it's created, you can apply rules to it.
If you want to apply your own policy instead of the default one then use the -p flag:
For example:
$ datree test ~/.datree/k8s-demo.yaml -p My_policy
